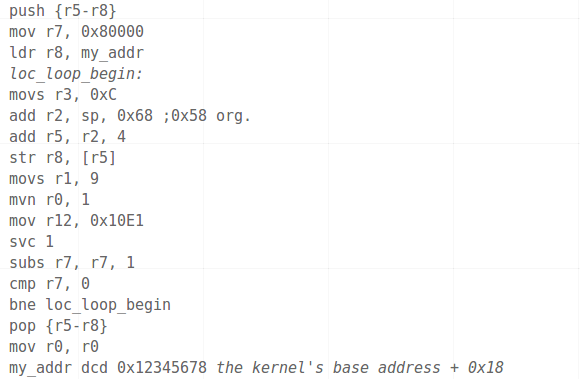
A crack has been found in the armor of Windows RT. This subset of Windows 8 is designed to run on ARM processors. The payload listed in the image above allows you to run unsigned desktop applications on the OS.
We haven’t seen very much about the Windows RT package, so it’s nice to hear [Clrokr's] thoughts on it. As far as he can tell the system has not been watered down from its Intel-aimed (x86) counterpart. Rather, RT seems to be a direct port with what is called “Code Integrity” mechanisms switched on. There is a kernel-level setting, barricaded behind UEFI’s Secure Boot, which determines the minimum software signing level allowed to run on the device. This is set to zero on a Windows 8 machine, but defaults to 8 on an ARM device. [Clrokr] uses a debugger to insert the code seen above into a DLL file in order to reset that minimum signing value to 0.
Do you have a project in mind for which this is useful? We’d love to hear about it in the comments!
[via Reddit]
Filed under: security hacks

